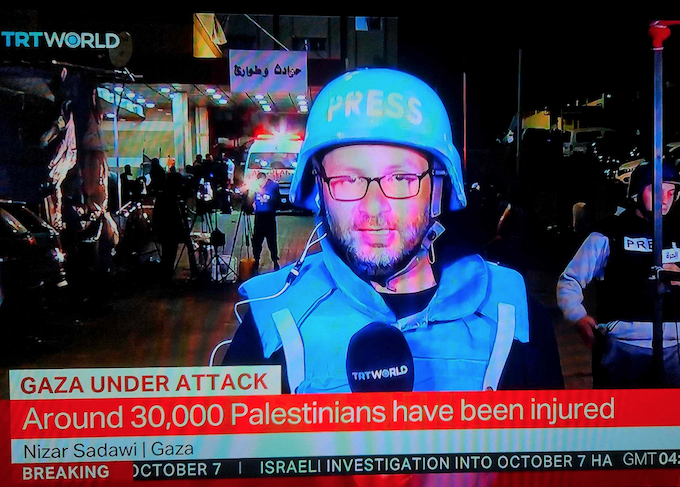
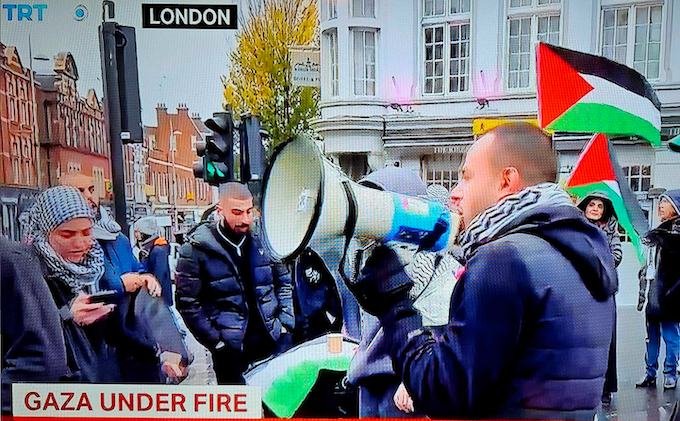
Americans have become easy prey for hackers, scammers, snitches, spies, and con artists.
But don’t be fooled into thinking the government is protecting you.
To the contrary, the U.S. government is selling us (or rather, our data) to the highest bidders.
By the way, those highest bidders also include America’s political class and the politicians aspiring to get elected or re-elected. As the Los Angeles Times reports, “If you have been to a political rally, a town hall, or just fit a demographic a campaign is after, chances are good your movements are being tracked with unnerving accuracy by data vendors on the payroll of campaigns.”
Your phones, televisions and digital devices are selling you out to politicians who want your vote.
“Welcome to the new frontier of campaign tech — a loosely regulated world in which simply downloading a weather app or game, connecting to Wi-Fi at a coffee shop or powering up a home router can allow a data broker to monitor your movements with ease, then compile the location information and sell it to a political candidate who can use it to surround you with messages,” writes journalist Evan Halper.
In this way, “we the people” have been reduced to economic units to be bought, bartered and sold by all and sundry.
On a daily basis, Americans have been made to relinquish the most intimate details of who we are—our biological makeup, our genetic blueprints, and our biometrics (facial characteristics and structure, fingerprints, iris scans, etc.)—in order to navigate an increasingly technologically-enabled world.
Those intimate details, in turn, have become the building blocks of massive databases accessed by the government and its corporate partners in crime, vulnerable to data breaches by hackers, cyberattacks and espionage.
For years now, and with little real oversight or restrictions, the government has been compiling massive databases comprised of all manner of sensitive information on the citizenry.
Biographical information. Biometric information. Criminal backgrounds. Travel records.
There is not a single person in the U.S. who is not in some government database or another, and these databases are increasingly being shared between agencies, fusion centers, and the police.
The government has also, with little oversight and few guidelines, been adding to its massive trove of data on Americans by buying commercially available information (CAI) from third-party sources. As a report by the Office of the Director of National Intelligence revealed:
“[Commercially purchased data] can reveal sensitive and intimate information about the personal attributes, private behavior, social connections, and speech of U.S. persons and non-U.S. persons. It can be misused to pry into private lives, ruin reputations, and cause emotional distress and threaten the safety of individuals. Even subject to appropriate controls, CAI can increase the power of the government’s ability to peer into private lives to levels that may exceed our constitutional traditions or other social expectations.”
In other words, this is the diabolically sneaky way in which the government is attempting to sidestep the Fourth Amendment, which requires that government agents have probable cause and a warrant before spying on Americans or searching and seizing their private property.
It’s bad enough that the government is building massive databases comprised of our personal information without our knowledge or consent, but then they get hacked and we suffer for it.
Earlier this year, for instance, several federal agencies, state governments and universities were targeted in a global cyberattack that compromised the sensitive data of millions of Americans.
Did that stop the government’s quest to keep building these databases which compromise our privacy and security? Of course not.
In fact, the government has also been selling our private information. According to Vice, Departments of Motor Vehicles in states around the country have been selling drivers’ personal information “to thousands of businesses, including private investigators who spy on people for a profit.”
Where there’s a will, there’s a way, and the government has become a master at finding loopholes that allow it to exploit the citizenry.
Thus, although Congress passed the Driver’s Privacy Protection Act (DPPA) in 1994 to prevent the disclosure of personal information, it hasn’t stopped state DMVs from raking in millions by selling driver data (names, dates of birth, addresses, and the cars they own) to third parties.
This is just a small part of how the government buys and sells its citizens to the highest bidders.
The why is always the same: for profit and power, of course.
Welcome to the age of surveillance capitalism.
Have you shopped at Whole Foods? Tested out target practice at a gun range? Sipped coffee at Starbucks while surfing the web? Visited an abortion clinic? Watched FOX News or MSNBC? Played Candy Crush on your phone? Walked through a mall? Walked past a government building?
That’s all it takes for your data to be hoovered up, sold and used to target you.
Incredibly, once you’ve been identified and tracked, data brokers can travel back in time, digitally speaking, to discover where you’ve been, who you’ve been with, what you’ve been doing, and what you’ve been reading, viewing, buying, etc.
Once you’ve been identified in this way, you can be tracked endlessly.
No one is spared.
In this regard, we are all equals: equally suffering the indignity of having every shred of privacy stripped away and the most intimate details of one’s life turned into fodder for marketers and data profiteers.
This creepy new era of for-profit surveillance capitalism—in which we’re being listened to, watched, tracked, followed, mapped, bought, sold and targeted—is made possible with our cooperation.
All those disclaimers you scroll though without reading them, the ones written in minute font, only to quickly click on the “Agree” button at the end so you can get to the next step—downloading software, opening up a social media account, adding a new app to your phone or computer—those signify your written consent to having your activities monitored, recorded and shared.
Think about it.
Every move you make is being monitored, mined for data, crunched, and tabulated in order to form a picture of who you are, what makes you tick, and how best to influence and/or control you.
With every smartphone we buy, every GPS device we install, every Twitter, Facebook, and Google account we open, every frequent buyer card we use for purchases—whether at the grocer’s, the yogurt shop, the airlines or the department store—and every credit and debit card we use to pay for our transactions, we’re helping Corporate America build a dossier for its government counterparts on who we know, what we think, how we spend our money, and how we spend our time.
The technology has advanced so far that marketers (political campaigns are among the worst offenders) can actually build “digital fences” around your homes, workplaces, friends and family’s homes and other places you visit in order to bombard you with specially crafted messages aimed at achieving a particular outcome.
If anyone else stalked us in this way—tailing us wherever we go, tapping into our calls, reading our correspondence, ferreting out our secrets, profiling and targeting us based on our interests and activities—we’d call the cops.
Unfortunately, the cops (equipped with Stingray devices and other Peeping Tom technologies) are also in on this particular scam.
It’s not just the surveillance and the buying and selling of your data that is worrisome.
The ramifications of a government—any government—having this much unregulated, unaccountable power to target, track, round up and detain its citizens is beyond chilling.
Imagine what a totalitarian regime such as Nazi Germany could have done with this kind of unadulterated power.
Imagine what the next police state to follow in Germany’s footsteps will do with this kind of power. Society is definitely rapidly moving in that direction.
We’ve made it so easy for the government to stalk us.
Government eyes see your every move: what you read, how much you spend, where you go, with whom you interact, when you wake up in the morning, what you’re watching on television and reading on the internet.
Every move you make is being monitored, mined for data, crunched, and tabulated in order to form a picture of who you are, what makes you tick, and how best to control you when and if it becomes necessary to bring you in line.
Chances are, as the Washington Post has reported, you have already been assigned a color-coded threat assessment score—green, yellow or red—so police are forewarned about your potential inclination to be a troublemaker depending on whether you’ve had a career in the military, posted a comment perceived as threatening on Facebook, suffer from a particular medical condition, or know someone who knows someone who might have committed a crime.
In other words, you might already be flagged as potentially anti-government in a government database somewhere—Main Core, for example—that identifies and tracks individuals (so they can be rounded up and detained in times of distress) who aren’t inclined to march in lockstep to the police state’s dictates.
The government has the know-how.
As The Intercept reported, the FBI, CIA, NSA and other government agencies are increasingly investing in and relying on corporate surveillance technologies that can mine constitutionally protected speech on social media platforms such as Facebook, Twitter and Instagram in order to identify potential extremists and predict who might engage in future acts of anti-government behavior.
Surveillance, digital stalking and the data mining of the American people—weapons of compliance and control in the government’s hands, especially when the government can listen in on your phone calls, monitor your driving habits, track your movements, scrutinize your purchases and peer through the walls of your home—add up to a society in which there’s little room for indiscretions, imperfections, or acts of independence.
This is the creepy, calculating yet diabolical genius of the American police state: the very technology we hailed as revolutionary and liberating has become our prison, jailer, probation officer, stalker, Big Brother and Father Knows Best all rolled into one.
It turns out that we are Soylent Green.
The 1973 film of the same name, starring Charlton Heston and Edward G. Robinson, is set in 2022 in an overpopulated, polluted, starving New York City whose inhabitants depend on synthetic foods manufactured by the Soylent Corporation for survival.
Heston plays a policeman investigating a murder, who discovers the grisly truth about the primary ingredient in the wafer, soylent green, which is the principal source of nourishment for a starved population. “It’s people. Soylent Green is made out of people,” declares Heston’s character. “They’re making our food out of people. Next thing they’ll be breeding us like cattle for food.”
Oh, how right he was.
Soylent Green is indeed people or, in our case, Soylent Green is our own personal data, repossessed, repackaged and used by corporations and the government to entrap us.
We, too, are being bred like cattle but not for food.
Rather, as I make clear in my book Battlefield America: The War on the American People and in its fictional counterpart The Erik Blair Diaries, we’re being bred, branded, bought and sold for our data.
As the insidious partnership between the U.S. government and Corporate America grows more invasive and more subtle with every passing day, there’s virtually no way to opt out of these assaults on your digital privacy short of being a modern-day Luddite, completely disconnected from all technology.
What we desperately lack and urgently need is an Electronic Bill of Rights that protects “we the people” from predatory surveillance and data-mining business practices.
Without constitutional protections in place to guard against encroachments on our rights in the electronic realm, it won’t be long before we find ourselves, much like Edward G. Robinson’s character in Soylent Green, looking back on the past with longing, back to an age where we could speak to whom we wanted, buy what we wanted, think what we wanted without those thoughts, words and activities being tracked, processed and stored by corporate giants such as Google, sold to government agencies such as the NSA and CIA, and used against us by militarized police with their army of futuristic technologies.

This post was originally published on Dissident Voice.

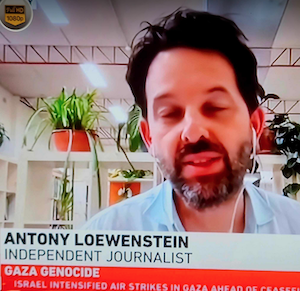
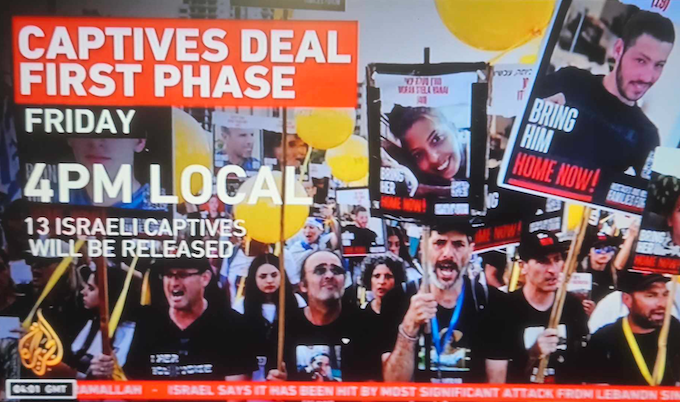
 Loewenstein warned in his book before the conflict began that “an Israeli operation might be undertaken to ensure a mass exodus, with the prospect of Palestinians returning to their homes a remote possibility” (p. 211).
Loewenstein warned in his book before the conflict began that “an Israeli operation might be undertaken to ensure a mass exodus, with the prospect of Palestinians returning to their homes a remote possibility” (p. 211).